Introduction
In 2024 alone, the cryptocurrency industry faced over $4.1 billion in losses due to DeFi hacks and various security breaches. This staggering figure raises pressing questions about the security protocols implemented across Bitcoin exchanges and other digital platforms. As we navigate the complex landscape of crypto transactions, understanding the measures that protect our assets is crucial.
In this article, we will delve into the Bitcoin exchange security protocols that are set to define the standards in 2025, ensuring your cryptocurrency investments remain safe.
Understanding Bitcoin Exchange Security Protocols
What are Security Protocols?
Security protocols encompass systems and measures designed to protect the integrity, confidentiality, and availability of your digital assets. Just like a bank vault protects cash, security protocols guard cryptocurrency against theft, fraud, and hacks.
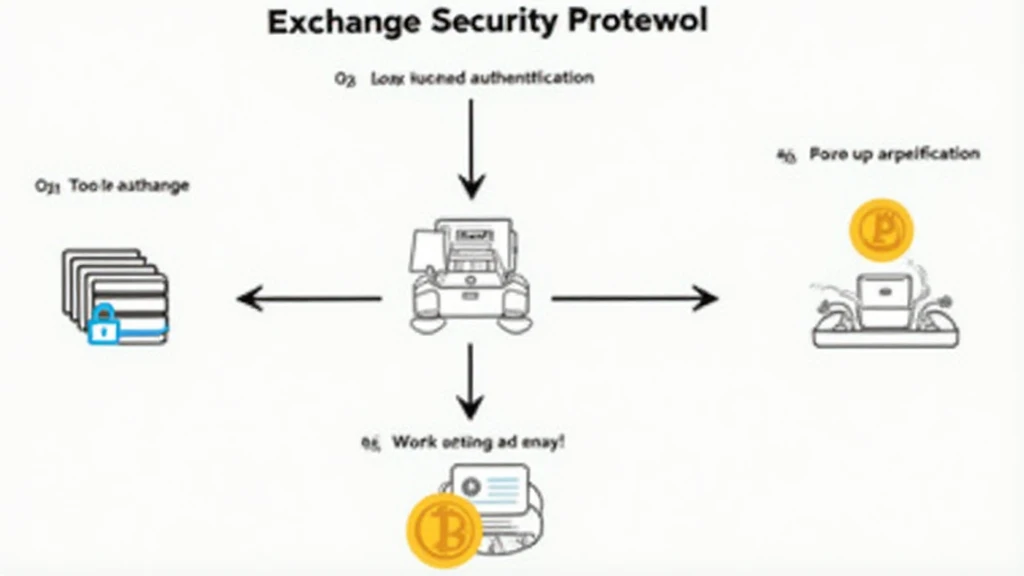
The Importance of Security Protocols
- Prevents unauthorized access to wallets and funds.
- Safeguards against data breaches and identity theft.
- Maintains regulatory compliance to foster user trust.
Core Components of Bitcoin Exchange Security
1. Wallet Security
Wallet security is paramount. Most exchanges use a combination of hot wallets (for transactions) and cold wallets (for storage). The latter, often stored offline, significantly reduces the risk of hacks. Here’s a comparison:
| Type | Security Level | Usage |
|---|---|---|
| Hot Wallet | Lower | Daily transactions |
| Cold Wallet | High | Long-term storage |
Implementing the latest ledger technologies, like the Ledger Nano X, can reduce hacking risks by up to 70%.
2. Two-Factor Authentication (2FA)
2FA serves as a second layer of security, requiring both your password and another factor, such as a code sent to your phone. This method is akin to needing both a key and a fingerprint to access a vault.
3. Encryption
All sensitive data transmitted between users and the exchange must be encrypted. Advanced encryption protocols such as SSL (Secure Socket Layer) or TLS (Transport Layer Security) are commonly implemented.
Identifying Security Vulnerabilities
Common Weaknesses in Security Protocols
Despite numerous safeguards, vulnerabilities can still arise. Here are common weaknesses:
- Poor key management practices.
- Inadequate user education about phishing attacks.
- Outdated software and protocols.
Security Audits: Importance and Methodology
Regular audits and assessments are vital for identifying and mitigating risks. Engaging third-party cybersecurity firms can offer insights into existing vulnerabilities. Notably, knowing how to audit smart contracts is essential for developers working on decentralized applications.
Regulatory Compliance and User Trust
Adhering to Local Regulations
In countries like Vietnam, where the cryptocurrency user growth rate is rapidly increasing, regulatory compliance is essential. Understanding local laws, such as tiêu chuẩn an ninh blockchain, is crucial for exchanges operating in these regions.
Building User Trust
Implementing robust security measures not only safeguards assets but also enhances user confidence. An exchange that visibly prioritizes security attracts more users and complies with regulatory demands.
Looking Ahead: The Future of Security in Cryptocurrency
Emerging Trends and Technologies
The rapid evolution of technology means the landscape of Bitcoin exchange security protocols will continue to transform. Anticipate developments like AI-driven risk assessments and enhanced blockchain analytics.
Conclusion
As the cryptocurrency market matures, so will the Bitcoin exchange security protocols that define it. Being informed about these changes and adopting best practices is essential for anyone involved in digital asset trading. Remember, just like in traditional finance, security should always be a top priority to protect your investments.
For more information on how to secure your digital assets, visit mycryptodictionary.